Privacy Enhancing Technologies, Simplified!

Privacy Enhancing Technologies, Simplified!
Rajesh Dangi, Jan 2021
The modern day battle of protecting privacy of user data is never ending and take great deal of efforts to win against websites or applications installed and running on your laptops, tablets, mobile phones and wearables. Although there is no silver bullet to achieve complete protection, the Privacy Enhancing Technologies ( Read, PETs) offer strategies and solutions that can help users regain some of their privacy that has been lost being online and connected to internet, the objective is to minimize possession of personal data without losing the functionality of usage and effectively control personal data sent to, gathered and used by, online service providers and application owners, merchants and or other online users / entities.
Conceptually PETs is been around from 80’s when measures were researched about security protocols, encryption techniques to protect emails, further in 90s it was extended for World Wide Web what we know as modern internet, websites and online applications etc by strengthening legal regulations and governance thereof. With globalization of economy and free flow of data between users, clouds and countries today we have standards and regulations governing data protection, acceptable usage and legal obligations of fiduciaries the PETs is already mainstream and got itself a seat in the boards of reputed corporates and cabinets of countries.
The struggle is not over and never will be, the technologies keep evolving and so do regulators trying to keep up to their core principle of protecting privacy of the PII data. The tools, processes and governing policies have seen radical shifts in recent years and paradigms have set tug of war between counties and corporations. There are dedicated initiatives like future of privacy forum, a think tank and advocacy group which is bringing the focus and the onus of privacy principles back to mainstream with responsible use technologies to garner principles of data protection and keep stakeholders focused on issues of data privacy.
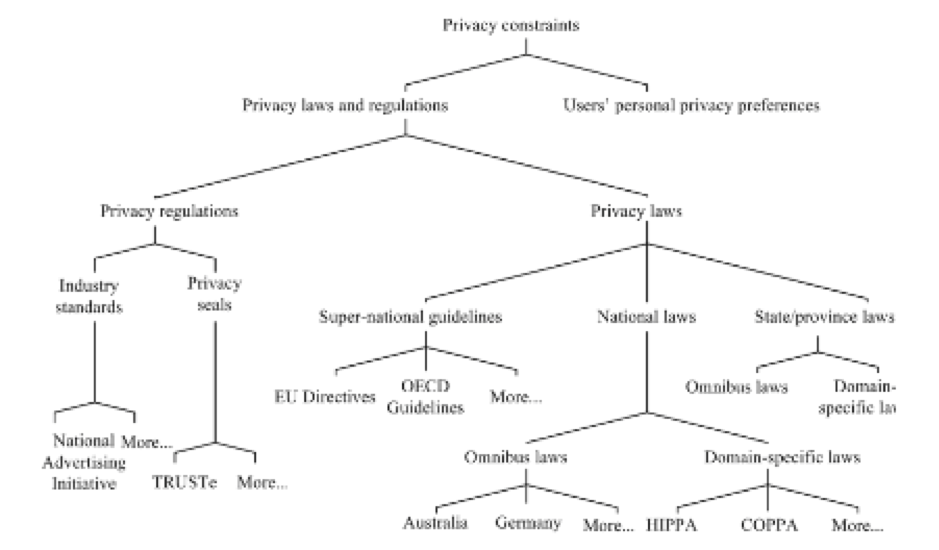
As of today, PETs have already established as an important tenet in the practical and theoretical aspects of privacy protection globally where data protection laws and systems are getting their right dues and regulations are being created enriching the value they offer.
Why PETs?
- PETs allows user to take action against their personal information which may be either sent to, or used by, third party service providers or users, also allows user to self-assess the need of sharing and establish control either by minimizing the personal data or anonymity of their personal information.
- Enabled user can achieve informed consent while giving their personal data to third parties.
- Provides the possibility to negotiate the terms and conditions (data handling/privacy policy negotiation) and ensures that both consumers and service providers establish, maintain, and refine privacy policies as individualized agreements through the ongoing choice amongst various service alternatives.
- Provide the possibility to have these negotiated terms and conditions technically enforced by the service provider thus ensuring trust with the consumers.
- All above arrangements with enforcements of terms and conditions can also be remotely audited to further strengthen the enforcement.
- Allows user or the person responsible to combine multiple PETs and other privacy advancing technologies that might also contribute to better privacy.
- Another important element of the PETs is that it allows users to track their own data flows, including what data has been transferred, when, to whom and under what conditions thus facilitating the basic principles of privacy choice & Consent, use limitation, collection limitation and also allows consumers to use their legal rights of data inspection, correction and deletion.
Implementation Approaches
The term Privacy Enhancing Technologies (PETs) represents broad spectrum of both old and relatively new and well-known techniques to minimize the exposure of private digital data. The scope of PETs is often depending on the usage scenario. The way PETs are defined, they may use various technical means via Encryption, Anonymization and Pseudonymisation in order to protect privacy by providing anonymity, pseudonymity, unlikability, and unobservability of data subjects.
Encryption, While this technique is at least as old as Roman Era and incorporated in most of the technologies these days, modern developments are now looking at Homomorphic encryption. This is a form of encryption that would allow calculations on encrypted data; a very exciting tech that could offer enhanced protection by never showing personal data in plain text yet make it accessible for authorized users or governments.
Anonymization is a very important technique for privacy protection which either encrypts or removes identifiable personal data from datasets, This way untrusted users can only access the datasets but not “relate to” the individuals’ identities. Important techniques within this category are Multi Party Computation, Differential privacy, Federated analysis, K-anonymity and anonymizing services like Off‐the‐Record messaging, Private information retrieval and Tor anonymization frameworks.
Pseudonymisation The General Data Protection Regulation (GDPR) has a very lengthy definition of pseudonymisation, but in essence it means: replacing identifying data with artificial identifiers. From that perspective, pseudonymous data still leaves some space for re-identification of data subjects and thus remains personal data, while anonymous data cannot be re-identified and would therefore fall outside the scope of personal data. Pseudonymisation methods include techniques such as : Scrambling, Masking, Tokenization and Data blurring etc.
Identity protector is another technique being used as a system element is used within the data system to convert the identity of the user involved (as the 'data subject') into one or more pseudo-identities. Thus the use of an identity protector makes it possible to intervene preventively within the data system to hide the identity of the person involved along with implementation techniques such as digital signatures, blind digital signatures, digital pseudonyms, digital certificates, etc.
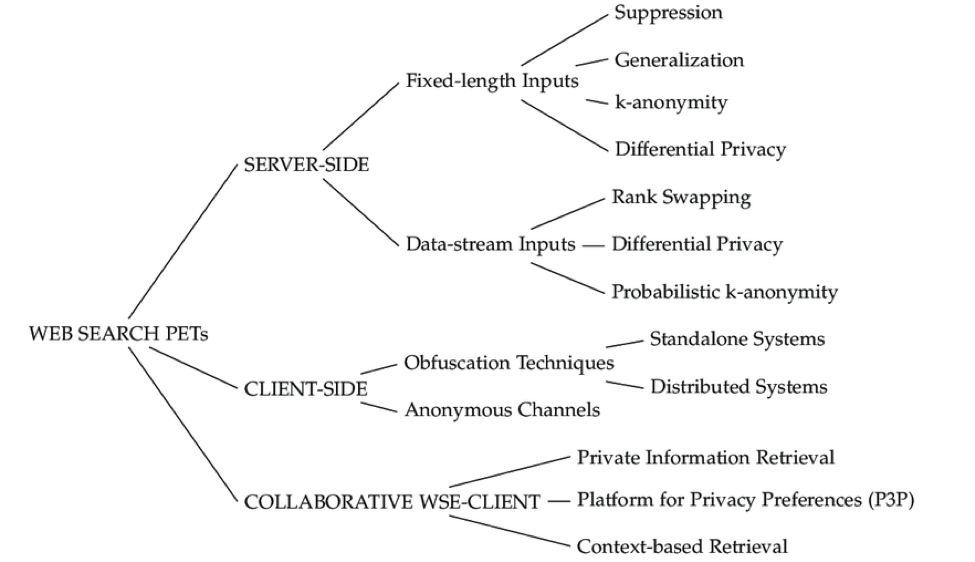
Promising PETs for privacy-aware data collection, analysis and dissemination
- Homomorphic encryptionAs mentioned above, homomorphic encryption schemes make it possible to run computations or processing on encrypted data without decrypting it. For example RSA encryption, which is commonly used in establishing secure connections through SSL/TLS. Some examples of PHE include ElGamal encryption (a multiplication scheme) and Paillier encryption (an addition scheme).
- Trusted executionare those physical environments that provide a hardware-based tools or solution that isolates data and code so that they cannot be read by the operating system or hypervisor involved in running the computations. A typical example is HSM – Hardware Security Modules
- Secure multiparty computation (SMPC) This technique enables private distributed computations on combined data without the separate parties sharing the data. with the goal of creating methods for parties to jointly compute a function over their inputs while keeping those inputs private, the cryptography in this model protects participants' privacyfrom each other. There are many SMPC frameworks available to explore..
- Differential privacy, which addresses privacy in disclosure rather than in computation, is a system for publicly sharing information about a dataset by describing the patterns of groups within the dataset while withholding information about individuals in the dataset. The differential privacy is as a constraint on the algorithms used to publish aggregate information about a statistical databasewhich limits the disclosure of private information of records whose information is in the database thus protecting data individuality and private algorithms provably resist identification and reidentification
- Personal data stores (PDS) refer to consumer apps and services that are supported by different kinds of PETs and enable people to have more control over their data. Personal data servicesor personal data stores (PDS) are services to let an individual store, manage and deploy their key personal data in a highly secure and structured way with central point of control with data attributes being managed by the service that may be stored in a co-located repository, or they may be stored multiple external distributed repositories, or in a combination.
- The Platform for Privacy Preferences (P3P) was created by the World Wide Web Consortium (W3C) with the objective of making easier for users to obtain information about the privacy policies of the sites that they visit. P3P is a framework through which users can automate the protection of their privacy. They can define their privacy preferences and, when a website does not conform to these preferences, then P3P-enabled browsers may alert the user and even take pre-established actions.
Global perspective on Privacy Laws
In response to Privacy concerns, many laws, regulations came out with their own set of privacy principles. Some of these include the Organization for Economic Cooperation and Development (OECD) privacy guidelines, the European Union (EU) Data Protection Directive (DPD), Canadian Personal Information Protection and Electronic Documents Act (PIPEDA), Asia-Pacific Economic Cooperation’s (APEC) Privacy Framework, etc.
Although there are commonalities between various privacy frameworks and guidelines, the way consumer privacy is perceived is different. For example, the European Union addresses privacy of personal information through one omnibus law and through an identified and independent data protection authority, while the United States addresses consumer privacy through sector specific and state laws on privacy of customer data that are administered by a variety of agencies. These include laws for protecting health information, and financial information among others. These laws are further supplemented by a variety of self-regulatory mechanisms and organizations.
India, At the moment does not have a specific legislation enacted primarily for data protection. India’s regulatory mechanism for data protection and privacy is the Information Technology Act, 2000 (“the IT Act”) and its corresponding Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal Data or Information) Rules, 2011 (“the IT Rules”).
In addition to this, Supreme Court of India has recognised the right to privacy as a fundamental right under Article 21 of the Constitution as a part of the right to “life” and “personal liberty”. “Informational privacy” has been recognised as being a facet of the right to privacy and the court held that information about a person and the right to access that information also needs to be given the protection of privacy. Fundamental rights are enforceable only against the state and instrumentalities of the state and the Supreme Court in the same judgment recognised that enforcing the right to privacy against private entities may require legislative intervention.
The Government of India therefore constituted a committee to propose a draft statute on data protection. The committee proposed a draft law and the Government of India has issued the Personal Data Protection Bill 2019 (“PDP Bill”) based on the draft proposed by the committee. After further deliberations the Bill was approved by the cabinet ministry of India on 4 December 2019 and tabled in the Lok Sabha on 11 December 2019.
In summary..
The potential violations of consumer and citizen privacy increase consequentially. However, PETs offers solutions in the shape of privacy protection for user, consumer and citizen and are becoming a promising aid to achieve basic privacy norms in lawful user data management in both online and offline state. PETs must have a definite thought process to the core of privacy by design, This is the needs of the hour demand in conceptual system design and engineering, where the relevant standards for privacy are kept in mind from the very outset in the development of applications, hosted infrastructure, business practices, products, and services and datasets.
The current generation of all digital systems rely on using individuals personal identity at various points for authentication and authorization privileges to server the intended content or facilitate transactions, fundamental question is whether it is necessary for the system to know the user’s identity, usage of other applications, contents of SMSs, call records and associated metadata or digital footprints such as location, personal attributes, activity logs etc using it even after the purpose of engagement is served or the application sessions ends.
Yet there are array of practical reasons appears to hamper the implementation of PETs. Often mentioned reasons are costs, legacy information systems, complex organizational processes, lack of expertise, awareness of privacy regulations and most important lack of intent, the price for which is being paid by the users inadvertently, for sure!!
***
Sept 2020. Compilation from various publicly available internet sources, authors views are personal.